Windows 10 and security are often mentioned in the same breath these days because Microsoft keeps adding new capabilities. Windows Hello for Business (WHfB) is a new feature available in Windows 10 that strengthens security and simplifies sign-in. In this blog, I’ll show you how to enable WHfB using Group Policy, Configuration Manager, or Intune.
Overview of Windows Hello for Business
WHfB acts a smart card on a Windows 10 machine, allowing for easier sign-in by requiring only a PIN or biometric. It creates more secure credentials challenge, going beyond the normal username and password combinations because it is device-specific.
A WHfB sign-in further increases security because it cannot be used to remotely access a machine, and the bits are different for every machine. This means that you must have physical access to a machine to use it, and the PIN or biometric is not transferable. While a user can use the same PIN or biometric data on multiple machines, the session or hash from one machine cannot be used to accessed another.
WHfB uses the Trusted Platform Module (TPM) chip on a machine to house the keys to unlock the machine. The PIN or biometric is used to “unlock” the keys in the TPM chip, which grants access to the machine. WHfB can be used on on-prem domain-joined, Azure AD-joined, or Intune-managed devices (even those that are not joined to on-prem or Azure AD).
There are three ways to enable WHfB: Group Policy, Configuration Manager, or Intune. All three methods set the same registry keys on the device, so if you’re using more than one (e.g., Group Policy and Intune) you probably want to ensure that they are delivering the same settings.
Enabled WHfB – Group Policy
For Group Policy, the relevant settings are at Computer Configuration > Administrative Templates > Windows Components > Windows Hello for Business. There are some biometric-specific settings in another location that we’ll talk about later.
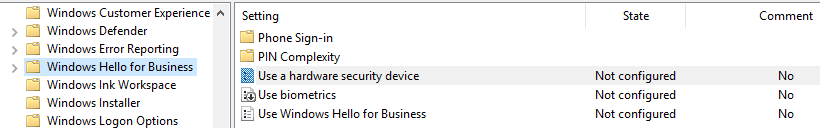 At the root of this folder are three settings. We’re concerned with the first and third settings from my screenshot. As of this writing, the “Use biometrics” setting does nothing to a device.
At the root of this folder are three settings. We’re concerned with the first and third settings from my screenshot. As of this writing, the “Use biometrics” setting does nothing to a device.
First, enabling “Use a hardware security device” requires that a machine has a TPM chip to use WHfB. Using a TPM is obviously more secure. If a device does not have a TPM, WHfB will use software to store the PINs. This setting will prevent that. If you enable this setting, WHfB will only function on a device with a TPM. Devices lacking a TPM will still function, but without WHfB.
Next, “Use Windows Hello for Business” simply enables WHfB (basically the same as not configured). Disabling this setting will prevent users from using WHfB. I recommend leaving this setting as “Not Configured” because it disables the ability to set a PIN, which is a requirement for WHfB.
PINs
Another folder within the WHfB GPO folder that we need to pay attention to is “PIN Complexity”. Before we look at the specific settings, we need to address how to enable PINs. By default, PINs are disabled as soon as you join a device to an on-prem domain. There’s a setting in Group Policy to enable PINs, but it’s restricted to only Windows 8 and 8.1. The registry key that this setting writes also applies to Windows 10, so I suggest adding it as a Group Policy preference registry key. Add this key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System
AllowDomainPINLogon=dword:00000001
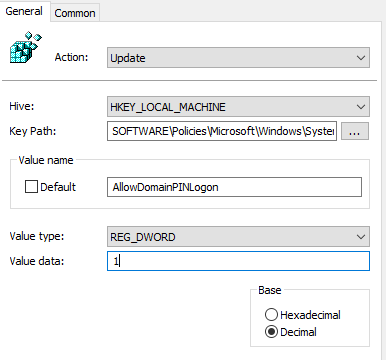
It’s also very important to leave the above-mentioned “Use Windows Hello for Business” GPO setting as “Not Configured,” as this setting will overwrite this key. Once you write this key, the PIN complexity settings will apply.
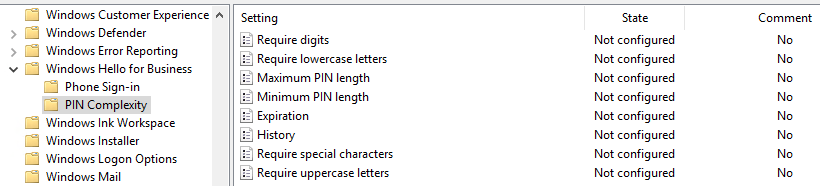
Within this directory, you can define all of the complexity requirements for a PIN. These are same complexity requirements you can configure for basic passwords. Some highlights are: PINs can be between 4 and 127 characters (configured with the maximum and minimum PIN length settings), you can set them to expire (0 means PINs do not expire, expiration can be set from 1 to 730 days), and the system can remember up to 50 PINs (with 0 being remember none).
Biometrics
I mentioned in the beginning of this section that the “Use biometrics” setting has no effect on the device. For biometric settings, go to Computer Configuration > Administrative Templates > Windows Components > Biometrics.
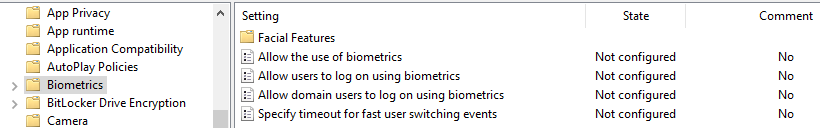
There aren’t many options. You can pretty much only disable them if you like using the “Allow the use of biometrics” setting.
Enable WHfB – Configuration Manager
Profiles for WHfB in ConfigMgr are located at Assets and Compliance > Compliance Settings > Company Resource Access > Windows Hello for Business Profiles.
Here’s the meat of the profile:
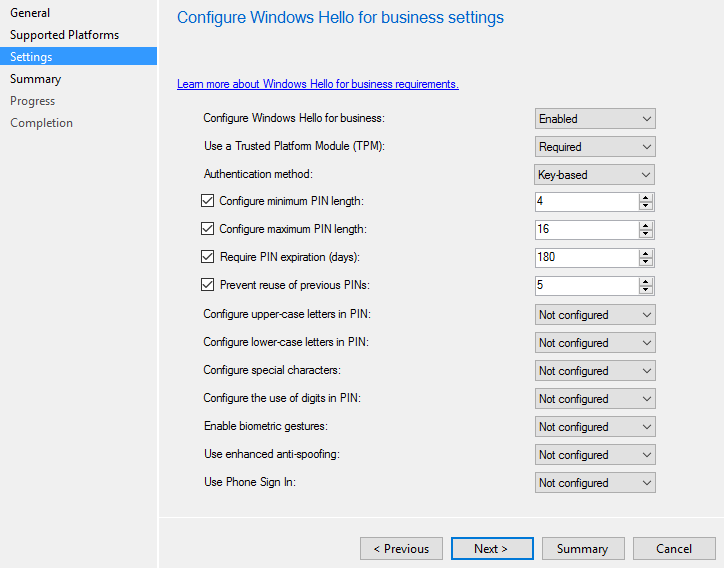 This example policy will enable WHfB and require the TPM module. It will set a minimum and maximum PIN length, as well as set it to expire and prevent the use of the last 5 PINs. After you have this configured, you have a policy that you can deploy to a collection. As you can see, you have the same settings available that you had via Group Policy.
This example policy will enable WHfB and require the TPM module. It will set a minimum and maximum PIN length, as well as set it to expire and prevent the use of the last 5 PINs. After you have this configured, you have a policy that you can deploy to a collection. As you can see, you have the same settings available that you had via Group Policy.
Like most things with ConfigMgr, it is recommended that you create a collection that does nothing but assign this policy. This makes troubleshooting issues much easier.
Enable WHfB – Intune
Finally, let’s look at the required settings for Intune. Intune creates a global policy, so you cannot target different settings at different machines. The settings are found under Admin > Mobile Device Management > Windows > Windows Hello for Business.
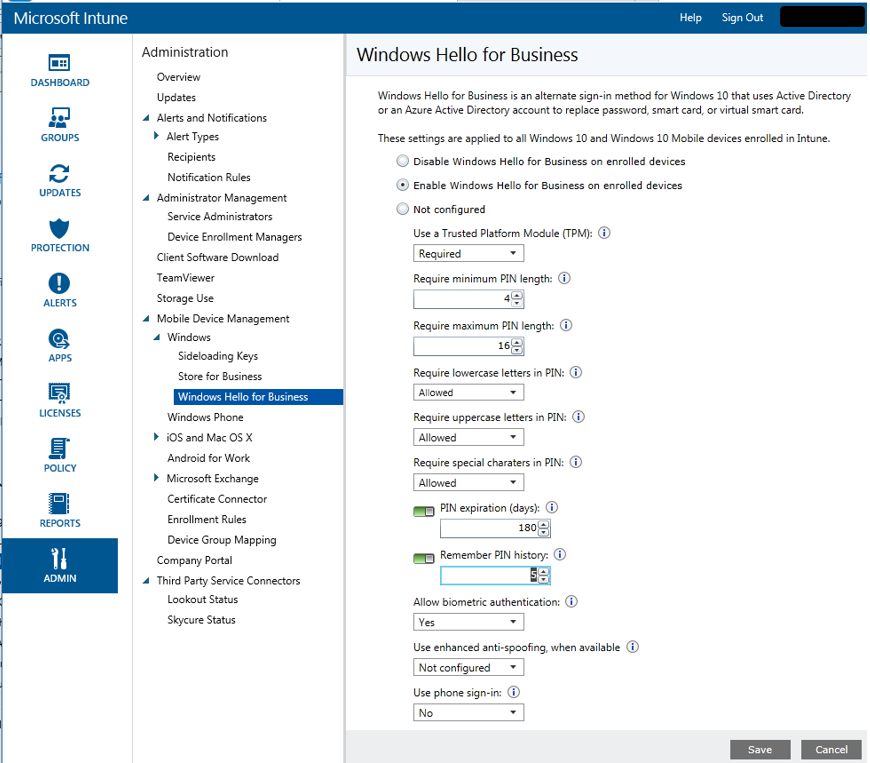 You have the same setting here that you had with ConfigMgr. Pay special attention though, because “Require lowercase letters in PIN,” “Require uppercase letters in PIN,” and “Require special characters in PIN” do not have a “Not Configured” option like they do in ConfigMgr. It’s Allowed, Required, or Not Allowed.
You have the same setting here that you had with ConfigMgr. Pay special attention though, because “Require lowercase letters in PIN,” “Require uppercase letters in PIN,” and “Require special characters in PIN” do not have a “Not Configured” option like they do in ConfigMgr. It’s Allowed, Required, or Not Allowed.
Once you save this policy, InTune will apply it to your Windows 10 devices.
Say Hello to WHfB
Hopefully, I’ve demystified your bigger questions about implementing Windows Hello for Business. It’s just one of so many ways you can boost security in Windows 10. As your Windows 10 footprint grows, you may look for automated solutions to ensure that all your endpoint have Windows Hello for Business and other security settings configured as desired.
Adaptiva Endpoint Health is a real-time automation engine that can automatically find and fix endpoint security and compliance issues company-wide. To learn more, request a demo today.




